Hello World! is iconically the most classic text display of an engineer’s first programming experience. We couldn’t think of a more fitting title for our first blog post, so without further ado, “Hello World!”

Cyber Defense Technologies (CDT) has been around for a while; our company was established over ten years ago. We’re a little late to the party with getting our blog up and running, but with October being National Cybersecurity Awareness month, we couldn’t think of a more fitting time to get started. We’re here and ready to share all things InfoSec!
Going forward this space will be a valuable resource (and/or possibly a meme repository). It will include information on securing your technology and devices, news about the Information Security (InfoSec) industry, technical demonstrations, and other important information you can utilize in your professional and personal life.
Who We Are
CDT specializes in providing comprehensive cyber security solutions primarily for government organizations of any size. Our team is comprised of highly skilled individuals with diverse infosec backgrounds in both the government and commercial sectors. We work to protect and secure systems to prevent cyber-attacks, breaches, and data loss.
Why Are We Here?
Point-blank – attackers are still getting in. While the specific modes of attack and popular exploits have changed, the reasons why they succeed have remained – defensive tactics stay the same and the basics of information security are often not implemented. Cyber Defense Technologies has been testing and identifying exploits for more than 10 years now and we continue to see existing vulnerabilities that have never been addressed such as:
- Unpatched or out-of-date software – WindowsXP, Windows 7, Windows 8 are all still running in the wild for many legitimate reasons, however, many are susceptible to very well-known exploitations such as MS08-067, MS17-010, MS10-018, and several others. Including internal/external vulnerability assessments in your security plan can help identify these systems and plan for mitigations which can help prevent breaches in your infrastructure.
- Default or weak passwords – Using usernames or seasons (i.e. Summer2020) as passwords or using vendor default passwords such as admin:admin pose risk to your systems. Routine assessments of your systems policies can help create and maintain a list of ‘in-use’ passwords that could lead to compromise.
- People are still clicking on phishing emails – When macros are enabled on your systems, phishing emails are much more successful when malicious attachments are involved. Internal testing, that includes phishing campaigns with these types of attachments, can test your protection mechanisms and highlight where your systems could fall with this type of attack. It will help you strategize how to protect against these types of attacks.
With the increasing use of technology and a larger reliance on digital data, the number of attacks continue to increase along with the volume and importance of data that is being exposed. With cybercrime like ransomware on the rise, it is important to take necessary steps to protect your information.
Check and Protect Your Information Security Basics
- Evaluate your enterprise; know what you have then seek to protect it. There can potentially be many avenues to gain access to a system and its information, it is crucial to identify all these areas in order to better secure your infrastructure.
- Turn on two-factor authentication for everything you can.
- Evaluate the use of automation tools. They help a good security engineer be a better engineer, but they do not stop all attacks – understand the scope and capability of the tools. To stop a hacker, you need to think like a hacker.
- Implement a security compliance framework (i.e. RMF, ISO 27001, PCI, etc).
- Understand compliance and security and the difference between the two. Compliance is and should be a continual process that needs constant nurturing, maintenance, and updates.
- Every system will have vulnerabilities and flaws and exposing them to your CISO and your internal IT teams will breed a culture of fixing the problems. Discovering vulnerabilities should not be looked at as an indication of bad security engineers or poorly implemented policies, rather, they are an opportunity to increase your defense strategies and better understand what bad actors can take advantage of to gain access to your systems.
- Patch Patch Patch! Unpatched systems are ‘calling-cards’ for bad actors. Bots and bad actors crawl the web 24 hours a day looking for exposed unpatched systems to exploit.
- Test Test Test! Get a penetration test and test the current level of your protection mechanisms. Annual penetration testing can help identify and mitigate vulnerabilities and test your defenses. New vulnerabilities and exploits are discovered almost daily. Continued testing can raise awareness to these newly developed strategies and how to best protect against them, as well, identify the ‘oldie-but-goodie’ well known exploits that can potentially exploit your systems.
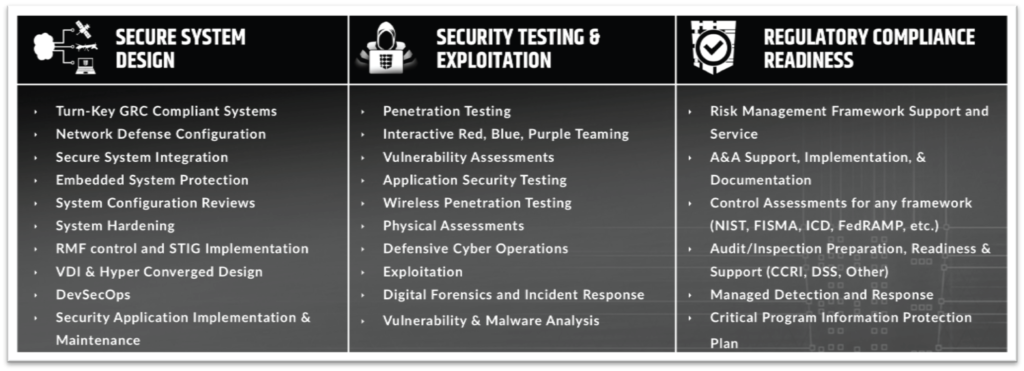
Our Services
CDT specializes in providing comprehensive cyber security solutions primarily for government organizations of any size.
| Veterans |

Veterans comprise over one-half of our team and we are an active member of the veteran community. As a Service-Disabled Veteran Owned Small Business, CDT supports many military-based organizations and donates a portion of our annual profits to veterans’ organizations. CDT also co-founded VetCon, which became an official event of the DefCon Hacker Conference, to connect and support Veterans in the Information Security field. As many events have turned virtual, so has VetCon (for now). We currently host a VetCon Discord server.
If you are or know a veteran in the InfoSec community join here: https://discord.gg/vetcon
Have any questions? Want to learn more? Have any good security memes? Feel free to reach out to us and follow us online.
